TL;DR
- Five password-protected computers contain crucial story details and unlock the Hard Work Trophy/Achievement
- Password puzzles follow consistent patterns combining dates with biographical or historical references
- Environmental observation and document collection are essential for solving all security challenges
- Advanced strategies help avoid common mistakes when navigating hostile environments during puzzle-solving
- Complete computer access reveals deeper narrative layers about the Federal Bureau of Control’s research
GameSpot may receive revenue from affiliate and advertising partnerships for sharing this content and from purchases through links.
Much like the investigative mechanics in Alan Wake 2 and Control, deciphering encrypted computer systems within the Lake House expansion provides essential narrative context and reveals hidden story elements. The Federal Bureau of Control research facility houses numerous classified documents behind digital security measures that players must systematically breach. Understanding the password puzzle framework early significantly enhances your exploration efficiency throughout the DLC.
The expansion features five distinct password-protected computer terminals that, when successfully accessed, collectively unlock the prestigious Hard Work Trophy/Achievement while delivering substantial lore revelations. While some systems demand straightforward code entry, others incorporate sophisticated environmental puzzles requiring keen observation and document correlation. Despite the limited number of secured terminals, overlooking crucial password clues remains surprisingly common when navigating the facility’s treacherous corridors under constant supernatural threat.
This comprehensive guide details every password-protected computer’s location within the Lake House, explains the methodology behind each security puzzle, and reveals the specific solutions. Complete password spoilers follow below, so proceed with caution if you prefer discovering solutions independently. For completionists determined to experience all narrative content, continue reading for expert guidance.
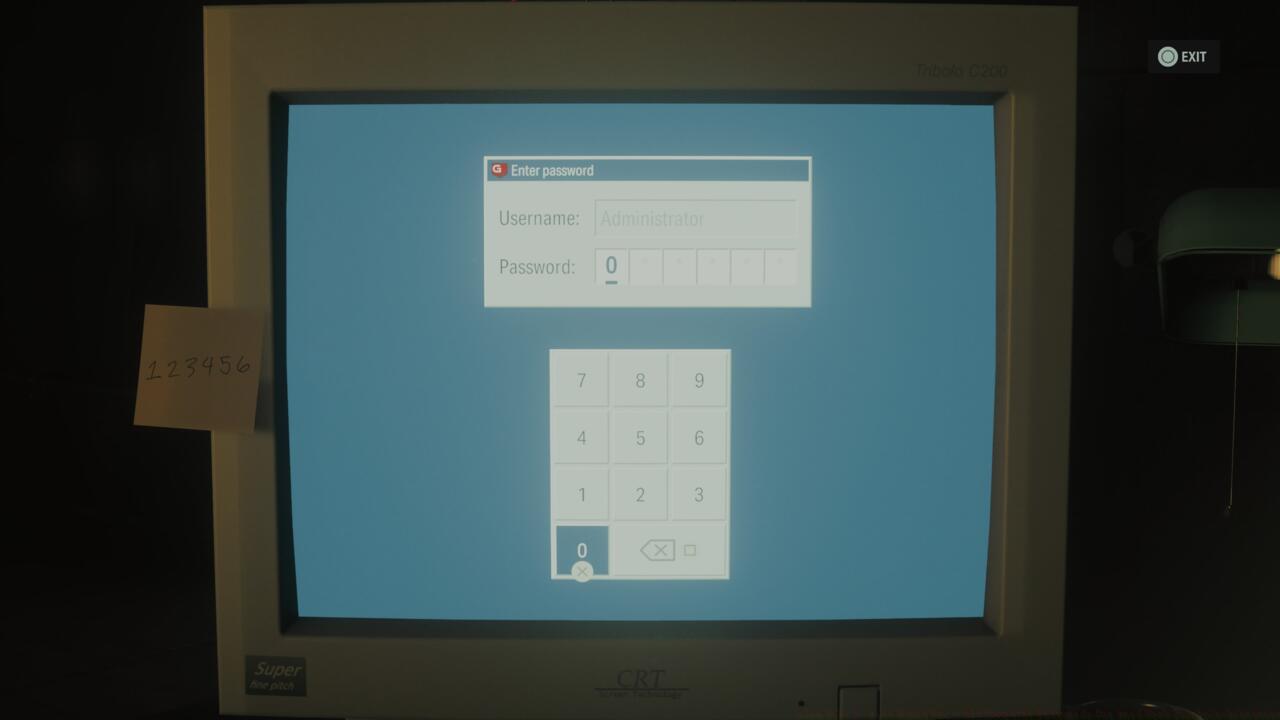
The initial computer security breach introduces players to the fundamental puzzle-solving methodology employed throughout the facility. To maintain operational security, Lake House personnel implement rotating six-digit access codes updated daily. The security protocol mandates consistent first four digits across systems while varying the final two characters for memorability. Despite explicit policies prohibiting personally identifiable dates like anniversaries or birthdays, compliance remains notoriously poor among researchers—fortunately for intruders.
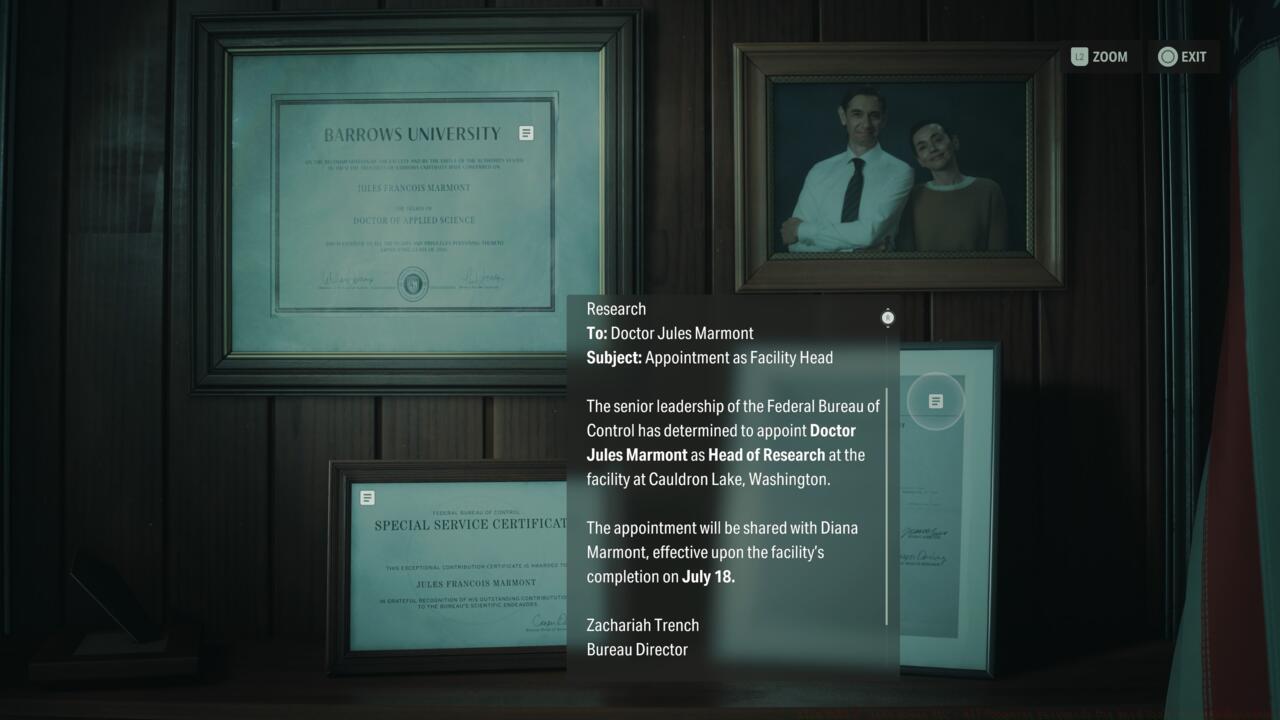
To decrypt Dr. Jules Mormon’s computer security, thoroughly investigate his office environment. Navigate to the corner section immediately right of the entrance doorway to locate the commemorative plaque marking when he and Dr. Diana Mormont initiated their joint leadership of Lake House research operations. This discovery provides the essential initial four numerical digits.
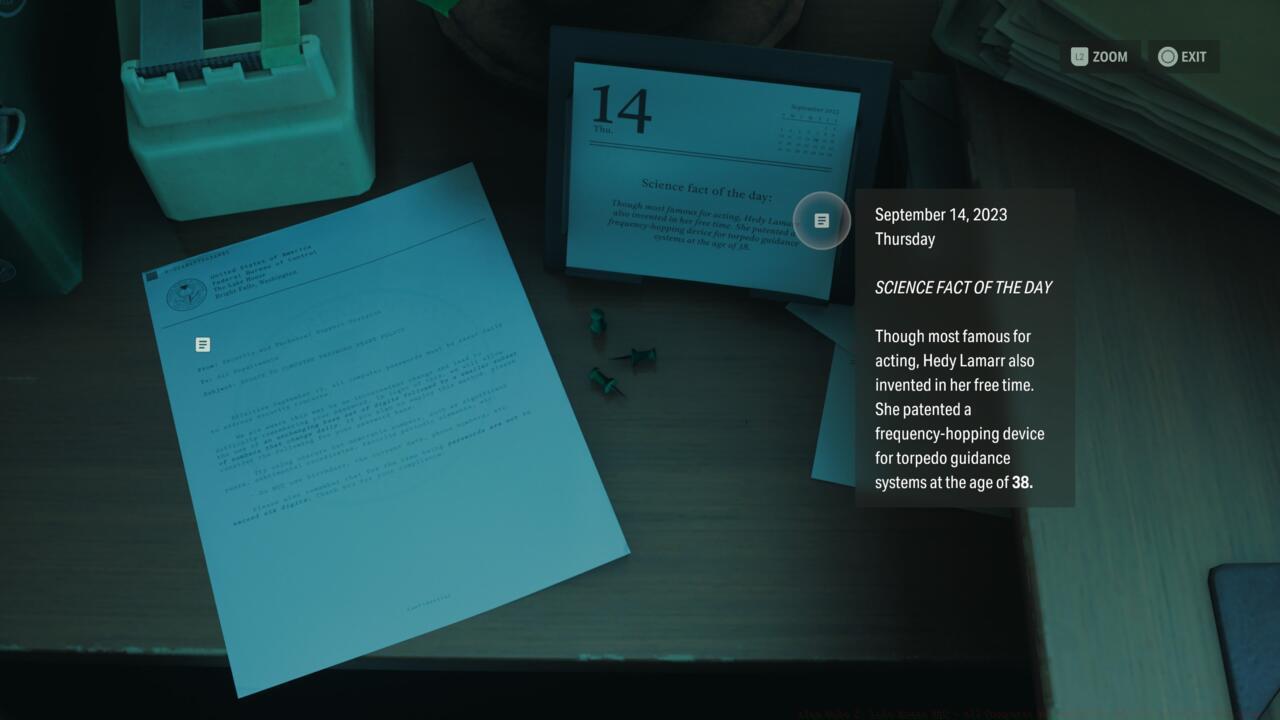
The concluding two digits originate from Jules’s desktop calendar notation referencing actress Hedy Lamar’s dual legacy as inventor, specifically highlighting her age during the frequency hopping innovation breakthrough.
Combining these discrete information fragments yields the complete access code: 071838

Upon reaching Sublevel 2, you’ll encounter comprehensive facility lockdown protocols with numerous Taken entities confined within separate office spaces. To deactivate emergency containment measures and restore door functionality, proceed to the distant sector of the level. During navigation, discover a chamber containing a computer interface adjacent to a observation window, with a deceased operative collapsed nearby. Search the remains to acquire the essential Clearance Level 2 access credential.
This terminal requires solving a multi-component puzzle utilizing intelligence scattered across documents in both the immediate room and adjacent areas. To compile necessary data, access the neighboring secured chamber using your newly obtained keycard. Within this auxiliary space, documentation confirms the password follows identical construction principles to Jules’s system—combining chronological dates with supplementary numerical references.


The Black Rock launcher room terminal on Floor -1 presents heightened security challenges requiring correlation of technical specifications with personnel records. Unlike earlier systems, this interface demands understanding the relationship between experimental equipment calibration data and researcher background information. Success requires meticulous examination of both operational logs and staff files scattered throughout the containment area.
Adjacent to the southern detention cell on Floor -2, another secured computer contains vital interrogation transcripts and observational records. The password derivation process involves cross-referencing prisoner identification numbers with security checkpoint timestamps found in adjacent monitoring stations.
Dr. Diane Mormont’s private office terminal on Floor -4 represents the most sophisticated security implementation. This system’s encryption combines elements from all previous puzzles while introducing new cryptographic elements based on the facility’s architectural layout and resonance frequencies.





Seasoned investigators recommend systematic documentation photography using the in-game camera feature to capture environmental details and written notes. This approach prevents backtracking through dangerous areas when puzzle components require simultaneous reference. A common oversight involves rushing through areas after obtaining keycards, missing subtle environmental clues integrated into room decorations and workstation arrangements.
Optimize your exploration by solving computer puzzles during initial area clearance rather than returning later. The constant respawn of Taken enemies in certain sectors makes repeated traversal increasingly hazardous. Allocate approximately 45-60 minutes for comprehensive computer access alongside main objectives.
The Hard Work Trophy/Achievement triggers immediately upon accessing the fifth secured terminal, accompanied by additional narrative revelations about the Federal Bureau of Control’s classified operations. For additional gaming strategy insights, consult our comprehensive Battlefield 6 Complete Guide for parallel investigative techniques.

Action Checklist
- Photograph all environmental details, plaques, and documents encountered during initial exploration
- Solve Dr. Jules Mormont’s computer first to understand password construction methodology
- Acquire Clearance Level 2 keycard before attempting Sublevel 2 terminals
- Systematically correlate date-based clues with biographical numerical references
- Access Dr. Diane Mormont’s office terminal last, as it incorporates elements from all previous puzzles
No reproduction without permission:SeeYouSoon Game Club » Alan Wake 2: Lake House DLC – All Computer Passwords For Hard Work Trophy/Achievement Complete guide to unlocking all five password-protected computers in Alan Wake 2's Lake House DLC with expert puzzle-solving strategies
